top of page
Search


Keeping Your Kids Safe Online: Protecting Against Internet Threats
The internet is an incredible resource for education, entertainment, and communication. However, it also comes with risks, especially for...
echoudhury77
Dec 17, 20243 min read
19 views
0 comments


Phishing and Smishing: Simple Ways to Stay Protected
Cybercriminals are constantly finding new ways to exploit individuals and organizations. Among the most common methods of attack are...
echoudhury77
Sep 12, 20243 min read
12 views
0 comments


State-Sponsored Cybercrime: Unmasking the Hidden Hands Behind Cyber Attacks
Cybercrime has evolved dramatically over the past decade, shifting from isolated hackers seeking financial gain to more sophisticated and...
echoudhury77
Sep 5, 20246 min read
15 views
0 comments
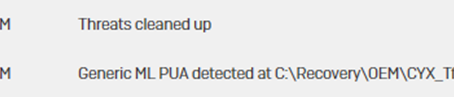
Product Evaluation: Acemagic S1
Acemagic is a popular technology company offering cheap computers and mini-PCs. Many are categorized as gaming computers by the company....
echoudhury77
Jan 12, 20243 min read
114 views
0 comments


Securing Your Online Accounts: Tips to Avoid Credential Stuffing Attacks
Digital interactions and transactions are an integral part of our daily lives. The security of online accounts is paramount....
echoudhury77
Jan 4, 20242 min read
20 views
0 comments


Domain Shadowing: Understanding the Threat
Cybersecurity evolves every minute. New threats and attack techniques constantly emerge, challenging organizations to stay one step ahead...
echoudhury77
Dec 15, 20233 min read
45 views
0 comments


The World of Brazilian Cyber Criminals
In the digital realm, where innovation and connectivity thrive, there exists a shadowy counterpart—cybercrime. Among the many nations...
echoudhury77
Dec 7, 20232 min read
20 views
0 comments


Notable Cyber Attacks - Nashville, TN
Nashville, Tennessee, known as the "Music City," is famous for its vibrant culture and thriving tech scene. However, it's not immune to...
echoudhury77
Oct 31, 20232 min read
21 views
0 comments


Unmasking the Shadows: The World of North Korean Hackers
In the interconnected world of cyberspace, North Korean hackers have emerged as a prominent and enigmatic threat. Operating under the...
echoudhury77
Oct 19, 20233 min read
14 views
0 comments


Ransomware Attacks: Unveiling the Chaos and Aftermath
Ransomware attacks are insidious, destructive cybercrimes that can paralyze individuals, businesses, and even critical infrastructure....
echoudhury77
Oct 19, 20232 min read
13 views
0 comments


Seven Reasons Why Trading Security for Convenience is Risky Business
In our fast-paced, tech-driven world, convenience is king. We all crave it, and businesses strive to provide it. Whether it's online...
echoudhury77
Oct 19, 20232 min read
25 views
0 comments


The Hidden Dangers of Unsecured Devices on Your Network
In a complex interconnected world, we rely on networks to facilitate communication and data exchange. However, this convenience comes...
echoudhury77
Oct 12, 20233 min read
28 views
0 comments


Smishing: Don't Get Hooked by Text Message Scams
In today's digital age, cybercriminals are continually finding new and creative ways to exploit unsuspecting individuals. While most...
echoudhury77
Sep 7, 20233 min read
15 views
0 comments


Protecting Your Business from the Growing Threat of Business Email Compromise
In today's digital age, businesses rely heavily on email communication for day-to-day operations, making it an essential tool for...
echoudhury77
Aug 11, 20233 min read
17 views
0 comments


SIM Swapping: The Dark Side of Mobile Security
In the age of smartphones and constant connectivity, our reliance on mobile devices for communication, banking, and accessing sensitive...
echoudhury77
Jul 19, 20232 min read
18 views
0 comments


The Art of Social Engineering: How Hackers Manipulate the Human Element
In the digital age, cybersecurity threats have become increasingly sophisticated, and hackers have developed ingenious methods to breach...
echoudhury77
Jul 19, 20233 min read
20 views
0 comments


Social Engineering: The Art of Human Hacking
Social engineering is a term that has become increasingly relevant in the world of cybersecurity. Despite the advancements in security...
echoudhury77
Apr 6, 20232 min read
30 views
0 comments


Credential Stuffing: Understanding the Threat and Protecting Your Data
In today's digital world, data breaches and cyberattacks are increasingly common occurrences. One of the prevalent and dangerous forms of...
echoudhury77
Apr 6, 20232 min read
21 views
0 comments


Secure Your Online Banking
Online banking has revolutionized the way we manage our finances, allowing us to conveniently access our accounts from anywhere, at any...
echoudhury77
Mar 28, 20232 min read
21 views
0 comments


Unraveling the World's Most Secretive Hacker Collective
North Korea, a country shrouded in secrecy, has garnered a reputation for its highly skilled and sophisticated cyber criminals. In a...
echoudhury77
Mar 21, 20233 min read
19 views
0 comments
bottom of page
