top of page
Search


The Role of AI in Our Daily Lives: Transforming the Present and Shaping the Future
Artificial Intelligence (AI) has become an integral part of our daily lives, often in ways we don’t even realize. From voice assistants...
echoudhury77
Feb 132 min read
5 views
0 comments


Keeping Your Kids Safe Online: Protecting Against Internet Threats
The internet is an incredible resource for education, entertainment, and communication. However, it also comes with risks, especially for...
echoudhury77
Dec 17, 20243 min read
19 views
0 comments


State-Sponsored Cybercrime: Unmasking the Hidden Hands Behind Cyber Attacks
Cybercrime has evolved dramatically over the past decade, shifting from isolated hackers seeking financial gain to more sophisticated and...
echoudhury77
Sep 5, 20246 min read
15 views
0 comments


BEC: A Deep Dive into Email-Based Cybercrime
Businesses heavily rely on email for communication, making email systems a prime target for cybercriminals. One of the most damaging and...
echoudhury77
Sep 5, 20245 min read
37 views
0 comments


China's National Security Law is a Global Threat
China's National Security Law, adopted on July 1, 2015, represents a significant milestone in the country's legal and political...
echoudhury77
May 30, 20243 min read
15 views
0 comments
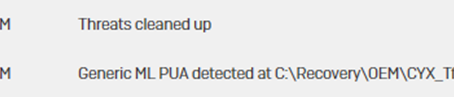
Product Evaluation: Acemagic S1
Acemagic is a popular technology company offering cheap computers and mini-PCs. Many are categorized as gaming computers by the company....
echoudhury77
Jan 12, 20243 min read
114 views
0 comments


Securing Your Online Accounts: Tips to Avoid Credential Stuffing Attacks
Digital interactions and transactions are an integral part of our daily lives. The security of online accounts is paramount....
echoudhury77
Jan 4, 20242 min read
20 views
0 comments


The World of Brazilian Cyber Criminals
In the digital realm, where innovation and connectivity thrive, there exists a shadowy counterpart—cybercrime. Among the many nations...
echoudhury77
Dec 7, 20232 min read
20 views
0 comments


Why the CEO Shouldn't Make Security Decisions
In today's digital age, cybersecurity is a paramount concern for businesses of all sizes. With data breaches and cyberattacks becoming...
echoudhury77
Oct 11, 20232 min read
22 views
0 comments


SIM Swapping: The Dark Side of Mobile Security
In the age of smartphones and constant connectivity, our reliance on mobile devices for communication, banking, and accessing sensitive...
echoudhury77
Jul 19, 20232 min read
18 views
0 comments


The Art of Social Engineering: How Hackers Manipulate the Human Element
In the digital age, cybersecurity threats have become increasingly sophisticated, and hackers have developed ingenious methods to breach...
echoudhury77
Jul 19, 20233 min read
20 views
0 comments


Russian Cyberthreats: Understanding the Landscape and Strengthening Your Defenses
In recent years, cyberthreats originating from Russia have become a significant concern for governments, organizations, and individuals...
echoudhury77
Apr 7, 20232 min read
35 views
0 comments


Social Engineering: The Art of Human Hacking
Social engineering is a term that has become increasingly relevant in the world of cybersecurity. Despite the advancements in security...
echoudhury77
Apr 6, 20232 min read
30 views
0 comments


Credential Stuffing: Understanding the Threat and Protecting Your Data
In today's digital world, data breaches and cyberattacks are increasingly common occurrences. One of the prevalent and dangerous forms of...
echoudhury77
Apr 6, 20232 min read
21 views
0 comments


Unraveling the World's Most Secretive Hacker Collective
North Korea, a country shrouded in secrecy, has garnered a reputation for its highly skilled and sophisticated cyber criminals. In a...
echoudhury77
Mar 21, 20233 min read
19 views
0 comments


When Insurance Companies Track you
Insurance companies may use geo tracking apps to monitor a policyholder's driving behavior and offer personalized discounts or adjust...
echoudhury77
Mar 13, 20232 min read
19 views
0 comments


The Risks of China-based Technology
The rise of Chinese technology companies has been a significant global phenomenon over the past decade. Companies like Huawei, ZTE, and...
echoudhury77
Mar 6, 20233 min read
11 views
0 comments


Biochips
Human identity chips, also known as microchips or biochips, are tiny devices that can be implanted under the skin to store personal...
echoudhury77
Mar 3, 20232 min read
76 views
0 comments


AI Language
ChatGPT is a language model developed by OpenAI. It is part of a family of models based on the transformer architecture, which has been...
echoudhury77
Mar 2, 20232 min read
79 views
0 comments


The Trouble with TikTok
TikTok has raised a lot of security concerns since it first became popular in 2018 after merging with Musical.ly. This platform is a...
echoudhury77
Feb 22, 20233 min read
34 views
0 comments
bottom of page
